A new report by Microsoft Security confirmed that Octo Tempest “leverages broad social engineering campaigns” to exploit organizations’ technological vulnerabilities in an effort to gain financial compensation. Social engineering is believed to be the tactic used to wreak havoc on MGM’s US casino hotels last month and extort a $15 million ransom payment from Caesars.
Social engineering can be as simple as hackers obtaining the name and title of a company’s staffer and then contacting the firm’s information technology (IT) department to request new login credentials. Octo Tempest initially caught the eyes of technology providers in early 2022 when it engaged in sim swaps for cash and hacked the cryptocurrency accounts of wealthy individuals.
Building on their initial success, Octo Tempest harnessed their experience and acquired data to progressively advance their motives, targeting, and techniques, adopting an increasingly aggressive approach,” noted Microsoft. “In late 2022 to early 2023, Octo Tempest expanded their targeting to include cable telecommunications, email, and technology organizations.”
Earlier this year, Octo Tempest is believed to have joined forces with ALPHV/BlackCat, which is a ransomware service (RaaS) outfit with ties to Scattered Spider.
Caesars, MGM Hackers Target Data-Rich Entities
In late 2022, the Octo Tempest/Scattered Spider morphed to focus on companies such as cable telecommunications, email, and technology organizations in an effort to procure customers’ sensitive data and leverage possession of that information for monetary gain.
Owing to the credit card-intensive nature of hotel bookings and the copious amounts of data accrued via loyalty programs, gaming companies are prime targets for cyber infiltrations and ransomware attacks.
“Octo Tempest progressively broadened the scope of industries targeted for extortion, including natural resources, gaming, hospitality, consumer products, retail, managed service providers, manufacturing, law, technology, and financial services,” added Microsoft.
While the list of companies, including Caesars, that have paid ransomware demands is lengthy, not all organizations meet threat actors’ financial demands. The FBI encourages ransomware victims to not pay up. MGM didn’t.
In fact, CEO Bill Hornbuckle recently said Scattered Spider waited several days before making its ransom demand. By that time, the casino operator was rebuilding its systems, and with that money already being spent, it wasn’t practical to compensate the hackers.
“The goal of Octo Tempest remains financially motivated, but the monetization techniques observed across industries vary between cryptocurrency theft and data exfiltration for extortion and ransomware deployment,” observed Microsoft.
Extortion, Sometimes Violent Threats Used
Ultimately, groups such as Octo Tempest and Scattered Spider aim to extract financial payments from victims. However, there are occasions when cyber threat actors resort to threats of violence and even a ploy known as “sextortion.”
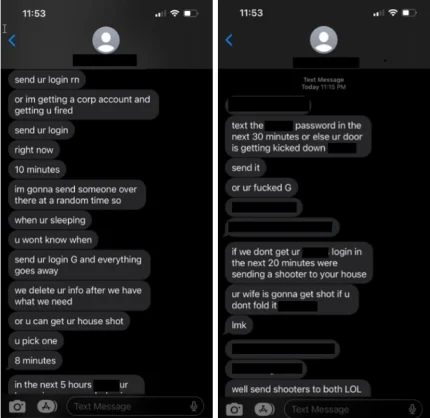
In rare instances, Octo Tempest resorts to fear-mongering tactics, targeting specific individuals through phone calls and texts. These actors use personal information, such as home addresses and family names, along with physical threats to coerce victims into sharing credentials for corporate access,” said Microsoft.
It’s not clear if such tactics were used against Caesars or MGM employees, but as the image below indicates, ransomware perpetrators can be aggressive in their attempts to get staffers to play ball.
https://www.casino.org/news/caesars-mg-hackers-extort-sometimes-threaten-violence/